- Home
- Information Technology
- Cyber Safe Sacramento
- Social Engineering
- City Departments
-
-
Community Development
-
Community Response
-
Convention and Cultural Services
-
Finance
-
Fire Department
-
Human Resources
-
Information Technology
-
Mayor and Council
-
Office of Public Safety Accountability
-
Office of the City Attorney
-
Office of the City Auditor
-
Office of the City Clerk
-
Office of the City Manager
-
Office of the City Treasurer
-
Police Department
-
Public Works
-
Utilities
-
Youth, Parks, & Community Enrichment
-
- Browse by categories
-
-
hiking Activities
-
pets Animals & Pets
-
domain_add Building & Planning
-
store Business
-
account_tree City Administration
-
category City Assets & Data
-
explore City Regions
-
diversity_4 Community Support
-
theater_comedy Culture & History
-
business_center Employment
-
directions Infrastructure
-
gavel Law, Code & Compliance
-
payments Money
-
park Outdoors & Sustainability
-
local_police Safety
-
directions_car Transportation
-
delete_sweep Utility Services
-
Use the menus above to navigate by City Departments or Categories.
- Convention and Cultural Services
- Arts and Culture
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Home
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Convention and Cultural Services
- Access Leisure
- Recreation
- Youth, Parks, & Community Enrichment
- Community Engagement
- Community Engagement
- About YPCE
- Hart Senior Center
- Recreation
- Older Adult Services
- Youth, Parks, & Community Enrichment
- Long Range
- Youth, Parks, & Community Enrichment
- Recreation
- Recreation
- Home
- Youth, Parks, & Community Enrichment
- About YPCE
- About YPCE
- Older Adult Services
- Home
- Innovation and Grants
- Aquatics
- CCS Partners
- Innovation and Grants
- Convention and Cultural Services
- Community Engagement
- District 7 - Rick Jennings
- Request a Permit
- CCS Partners
- Fire Department
- About YPCE
- Convention and Cultural Services
- CCS Partners
- Emergency Management
- CCS Partners
- Commercial Waste Services
- Home
- Recreation
- Access Leisure
- Recreation
- Recreation
- Recreation
- Specialty Parks
- Specialty Parks
- Permits for YPCE
- Recreation
- Youth, Parks, & Community Enrichment
- About YPCE
- Youth, Parks, & Community Enrichment
- Aquatics
- Home
- Animal Care
- Animal Care
- Community Development
- Animal Care
- Animal Care
- Animal Care
- Animal Care
- Animal Care
- Specialty Parks
- Animal Care
- Animal Care
- City Government
- Community Development
- Building
- Contact CDD
- Building
- Building
- Building
- Building
- Business Waste Requirements
- Commercial Waste Services
- Maintenance Services
- Procurement Services Division
- Parks
- Utilities
- Public Works
- Engineering
- Fire Prevention
- Building
- Building
- Building
- Building
- Engineering
- Home
- Public Works
- Engineering
- Planning
- Fire Prevention
- Contact CDD
- Building
- Fire Prevention
- Engineering Programs & Services
- Fire Prevention
- Community Development
- Community Development
- Community Development
- Transportation
- Locate & Grow in Sacramento
- Planning
- Planning
- Planning
- Climate Action Initiatives
- Planning
- Planning
- Parks
- Community Development
- Community Development
- Planning
- List of City Manager's Office Projects and Programs
- Public Works
- Planning
- Planning
- Public Works
- Transportation
- Planning
- Planning
- Engineering
- 102-Acre Site
- Community Development Meetings and Hearings
- Major Planning Projects
- Locate & Grow in Sacramento
- Planning
- City Government
- Innovation and Economic Development
- Code Compliance
- Revenue Division
- Business
- Office of the City Manager
- Recycling & Solid Waste
- Business
- Business
- Procurement Services Division
- Revenue Division
- Business
- Revenue Division
- City Auditor Reports
- City Auditor Reports
- Cannabis Management
- Cannabis Management
- Business Operations Tax
- Cannabis Management
- Office of the City Manager
- Cannabis Management
- Cannabis Management
- Cannabis Management
- Parking
- COVID-19 Relief & Recovery
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Office of the City Manager
- Business
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- Office of the City Manager
- Business
- Finance
- Accounting Division
- Police Services
- Procurement Services Division
- City Government
- Code Compliance Programs
- Code Compliance Programs
- Commercial Waste Services
- Procurement Services Division
- Procurement Services Division
- Home
- Commercial Waste Services
- Procurement Services Division
- Finance
- Finance
- Procurement Services Division
- Office of the City Auditor
- Office of the City Auditor
- Office of the City Auditor
- Accounting Division
- Office of the City Clerk
- Home
- About YPCE
- Diversity and Equity
- Records Management
- Office of the City Auditor
- Director Hearings
- Director Hearings
- Director Hearings
- District 1 - Lisa Kaplan
- District 2 - Shoun Thao
- City Auditor Reports
- Office of the City Clerk
- About YPCE
- Police Transparency
- Home
- Records Management
- Office of the City Manager
- Office of the City Manager
- Office of the City Manager
- Neighborhood Directory
- Neighborhood Directory
- Community Engagement
- Office of the City Manager
- Office of the City Manager
- Office of the City Manager
- Office of the City Manager
- Home
- City Government
- Engineering
- City Government
- Long Range
- City Government
- City Government
- City Government
- City Government
- Information Technology
- Camp Sacramento
- Parking
- About YPCE
- Finance
- Drinking Water Quality
- Office of Public Safety Accountability
- Police Services
- Police Services
- Marina
- Police Services
- Contact Us
- Police Services
- Utilities
- Pay Your Utility Bill
- Office of the City Clerk
- Home
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Office of the City Clerk
- Mayor and Council
- Home
- Diversity and Equity
- Office of the City Auditor
- Office of Public Safety Accountability
- About the City Attorney's Office
- Office of the City Auditor
- Office of the City Auditor
- Police Department
- Maps and Geographic Information Systems
- Office of Public Safety Accountability
- Police Department
- City Government
- Office of the City Auditor
- 102-Acre Site
- 102-Acre Site
- Public Works
- About SPD
- Facilities & Real Property Management
- Public Works
- Adult Sports Activities and Resources
- Climate Action Initiatives
- Fleet Services
- Public Works
- Director Hearings
- Director Hearings
- Director Hearings
- Director Hearings
- General Plans
- Police Transparency
- Convention and Cultural Services
- Legislative Management
- Home
- Maps and Geographic Information Systems
- Office of the City Clerk
- Police Services
- Office of the City Auditor
- Office of Public Safety Accountability
- About the City Attorney's Office
- Office of the City Auditor
- Office of the City Auditor
- Police Department
- Maps and Geographic Information Systems
- Office of Public Safety Accountability
- Police Department
- City Government
- Office of the City Auditor
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Maps and Geographic Information Systems
- Community Resources and Financial Empowerment
- Community Engagement
- Locate & Grow in Sacramento
- Major Planning Projects
- Engineering
- 102-Acre Site
- Community Development Meetings and Hearings
- Major Planning Projects
- Locate & Grow in Sacramento
- Planning
- Youth, Parks, & Community Enrichment
- Specialty Parks
- Long Range
- City Government
- List of City Manager's Office Projects and Programs
- Parking
- About YPCE
- Home
- Engineering Programs & Services
- Maintenance Services
- City Government
- Older Adult Services
- Home
- Youth, Parks, & Community Enrichment
- About YPCE
- About YPCE
- Older Adult Services
- Home
- 102-Acre Site
- Long Range
- City Auditor Reports
- Priority Projects/Investments
- Innovation and Economic Development
- Diversity and Equity
- Join Sacramento Fire
- Innovation and Economic Development
- Transportation
- Responding to Homelessness
- Office of the City Manager
- District 5 - Caity Maple
- Office of the City Manager
- Safety and Crime Prevention Tips
- Police Department
- Community Development Meetings and Hearings
- Diversity and Equity
- Older Adult Services
- Cannabis Management
- Office of the City Auditor
- Office of the City Auditor
- Human Resources
- Financial Empowerment
- Home
- Innovation and Economic Development
- Police Community Programs
- Community Response
- Community Response
- Workforce Development
- Police Community Programs
- Community Response
- Office of the City Manager
- Planning
- Housing
- Housing Development Toolkit
- Housing Development Toolkit
- Housing
- Housing
- Code Compliance
- Revenue Division
- Priority Projects/Investments
- Long Range
- About YPCE
- Older Adult Services
- Recreation
- Older Adult Services
- Youth, Parks, & Community Enrichment
- Older Adult Services
- Home
- District 5 - Caity Maple
- About the Office of the City Auditor
- Join Sacramento Fire
- Animal Care
- District 7 Resources
- Community Engagement
- Police Community Programs
- About YPCE
- Police Department
- Youth, Parks, & Community Enrichment
- Specialty Parks
- Aquatics Programs
- District 7 Resources
- Youth, Parks, & Community Enrichment
- CCS Partners
- Join Sacramento Fire
- About YPCE
- Aquatics Programs
- Recreation
- Aquatics
- Youth, Parks, & Community Enrichment
- Police Community Programs
- Youth, Parks, & Community Enrichment
- Youth, Parks, & Community Enrichment
- Police Community Programs
- Youth, Parks, & Community Enrichment
- Recreation
- Youth, Parks, & Community Enrichment
- Home
- Convention and Cultural Services
- Arts and Culture
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Home
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Convention and Cultural Services
- Innovation and Grants
- Aquatics
- CCS Partners
- Innovation and Grants
- Convention and Cultural Services
- Community Engagement
- District 7 - Rick Jennings
- Request a Permit
- CCS Partners
- Fire Department
- About YPCE
- Convention and Cultural Services
- CCS Partners
- Emergency Management
- CCS Partners
- Commercial Waste Services
- Home
- Convention and Cultural Services
- About the City Attorney's Office
- Specialty Parks
- Planning
- About Sacramento Fire
- CCS Partners
- Public Works
- Police Department
- Cannabis Management
- Office of the City Auditor
- Office of the City Auditor
- Human Resources
- Financial Empowerment
- Home
- Innovation and Economic Development
- Police Community Programs
- Human Resources
- Human Resources
- Human Resources
- Human Resources
- Home
- Human Resources
- Payroll Division
- Camp Sacramento
- HR Documents & Resources
- Human Resources
- Human Resources
- Home
- District 7 Resources
- Fire Department
- Leisure Enrichment
- Employee & Retiree Benefits
- Police Services
- START
- Passage Middle School Program
- District 5 - Caity Maple
- About the Office of the City Auditor
- Join Sacramento Fire
- Animal Care
- District 7 Resources
- Community Engagement
- Police Community Programs
- About YPCE
- Police Department
- Innovation and Economic Development
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Current Transportation Efforts, Plans and Programs
- Utilities
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Utilities
- Information Technology
- Information Technology
- City Government
- Information Technology
- Information Technology
- Information Technology
- Information Technology
- Home
- Fire Operations
- Information Technology
- Information Technology
- Collection Calendar
- City Government
- Information Technology
- Infrastructure Finance Division
- Home
- Infrastructure Finance Division
- Finance
- Infrastructure Finance Division
- Infrastructure Finance Division
- Building Programs
- Utilities
- Utilities
- Office of the City Manager
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Safety Tips
- Construction Coordination
- Transportation
- Transportation
- Utilities
- Public Works
- Public Works
- Police Community Programs
- Utilities Projects
- Home
- Survey Services
- Maintenance Services
- Utilities Projects
- Maintenance Services
- Maintenance Services
- Curbside Collection Services & Rates
- Tree Permits and Ordinances
- Public Works
- Transportation
- Transportation
- Engineering
- Transportation
- Transportation
- Park Planning & Development
- Parks
- Public Works
- Transportation Projects
- Parks
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Utilities
- Utilities
- Utilities
- Utilities
- Stormwater Quality
- Stormwater Quality
- Home
- Utilities
- Utilities
- Community Development
- Community Development
- Code Compliance
- Code Compliance
- Community Development
- Code Compliance
- Code Compliance
- Community Development
- Fire Prevention
- Code Compliance
- Recycling & Solid Waste
- Code Compliance
- Residential Permit Parking (RPP)
- Code Compliance
- Fire Prevention
- Contact CDD
- Building
- Fire Prevention
- Engineering Programs & Services
- Fire Prevention
- Commercial Waste Services
- Cannabis Management
- City Government
- Commercial Waste Services
- Recycling & Solid Waste
- Disabled Person Parking
- Fire Code Enforcement
- Commercial Waste Services
- Contact Parking Services
- Residential Permit Parking (RPP)
- Community Development
- Request a Permit
- Request a Permit
- Fire Prevention
- Contact CDD
- Public Records
- Code Compliance
- Cannabis Management
- Request a Permit
- Request a Permit
- City of Festivals
- Engineering
- Request a Permit
- Housing Development Incentives
- Arts and Culture
- Housing Development Incentives
- Public Works
- Public Works
- Building
- Youth, Parks, & Community Enrichment
- Locate & Grow in Sacramento
- Building
- Request a Permit
- Revenue Division
- Revenue Division
- Commercial Waste Services
- Building Programs
- Urban Forestry
- Planning
- Finance
- Accounting Division
- Home
- Accounting Division
- Payroll Division
- Curbside Collection Services & Rates
- Office of the City Manager
- Finance
- Budget Division
- Budget Division
- Home
- Hart Senior Center
- Recycling & Solid Waste
- Discount Deals
- Water Conservation
- Aquatics
- Finance
- Pay Your Utility Bill
- Utility User Tax
- Office of the City Treasurer
- Office of the City Treasurer
- Home
- Office of the City Treasurer
- Parking
- COVID-19 Relief & Recovery
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Office of the City Manager
- Business
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- CORE
- Innovation and Grants
- Convention and Cultural Services
- Stormwater Quality
- Economic Gardening
- Arts and Culture
- Innovation and Grants
- Recycling & Solid Waste
- Youth, Parks, & Community Enrichment
- Engineering
- Infrastructure Finance Division
- Home
- Infrastructure Finance Division
- Finance
- Infrastructure Finance Division
- Infrastructure Finance Division
- Building Programs
- Office of the City Treasurer
- Office of the City Treasurer
- Home
- Office of the City Treasurer
- Building
- Cannabis Business Operating Permits
- Revenue Division
- Development Standards
- Recycling & Solid Waste
- Development Standards
- Finance
- Community Engagement
- Marina
- Household Hazardous Waste
- Public Works
- Community Development
- Revenue Division
- Utilities
- City Government
- Finance
- Animal Care
- Home
- Development Standards
- Marina
- Revenue Division
- Permits for YPCE
- Revenue Division
- Infrastructure Finance Division
- Home
- Workforce Development
- List of City Manager's Office Projects and Programs
- About YPCE
- Revenue Division
- Budget Division
- Revenue Division
- Revenue Division
- Transportation
- Utilities Projects
- Climate Action Initiatives
- Housing
- Public Works
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Public Works
- Home
- Access Leisure
- Recreation
- Climate Action and Sustainability
- Climate Action and Sustainability
- Public Works
- Climate Action and Sustainability
- Climate Action and Sustainability
- Planning
- Fleet Services
- Climate Action and Sustainability
- Procurement Services Division
- Business Waste Requirements
- Permit Services
- Utilities
- Climate Action and Sustainability
- Utilities
- Recreation
- About YPCE
- Public Works
- Youth, Parks, & Community Enrichment
- About YPCE
- Commercial Waste Services
- Permits for YPCE
- About YPCE
- Home
- Current Transportation Efforts, Plans and Programs
- Recreation
- Access Leisure
- Recreation
- Recreation
- Recreation
- Specialty Parks
- Specialty Parks
- Permits for YPCE
- Recreation
- Youth, Parks, & Community Enrichment
- About YPCE
- Youth, Parks, & Community Enrichment
- Aquatics
- Home
- Park Planning & Development
- Parks
- Public Works
- Transportation Projects
- Parks
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Urban Forestry
- Parks
- Public Works
- Parks
- Home
- Urban Forestry
- Urban Forestry
- Urban Forestry
- Climate Action Initiatives
- Maintenance Services
- Safety Tips
- Office of the City Manager
- Specialty Parks
- Community Response
- Community Response
- Home
- Office of the City Manager
- Contact Us
- Contact Us
- Crime and Safety
- Crime and Safety
- Crime and Safety
- Crime and Safety
- Crime and Safety
- Police Services
- Fire Prevention
- Crime and Safety
- Police Services
- Crime and Safety
- Pay Your Utility Bill
- Crime and Safety
- Office of the City Auditor
- City Auditor Reports
- Fire Prevention
- Office of the City Manager
- Fire Department
- Join Sacramento Fire
- Crime and Safety
- Emergency Management
- Fire Department
- Fire Department
- Fire Department
- Home
- Fire Department
- Fire Department
- Fire Department
- Home
- Fire Department
- Fire Prevention
- Contact CDD
- Building
- Fire Prevention
- Engineering Programs & Services
- Fire Prevention
- Request a Permit
- Request a Permit
- Police Services
- Police Services
- Request a Permit
- Request a Permit
- Police Services
- Police Department
- Request a Permit
- Police Services
- Police Services
- Police Services
- Police Services
- Public Information Office
- Police Services
- Home
- Police Department
- Home
- Police Department
- Police Department
- Request a Permit
- Police Services
- Police Services
- Police Services
- Police Services
- Police Services
- Police Services
- Police Department
- Emergency Management
- Police Department
- Information Technology
- Flood Preparedness
- Fire Department
- Utilities
- Utilities
- Office of the City Manager
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Safety Tips
- Safety Tips
- Office of the City Manager
- Specialty Parks
- Transportation
- Utilities Projects
- Climate Action Initiatives
- Housing
- Public Works
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Public Works
- Home
- Transportation Technology
- Parking
- Fleet Services
- Climate Action Initiatives
- Current Transportation Efforts, Plans and Programs
- Police Services
- Marina
- Marina
- Public Works
- Housing
- Home
- Curbside Collection Services & Rates
- Sacramento Valley Station
- Public Works
- Long Range
- Current Transportation Efforts, Plans and Programs
- Transportation
- Public Works
- Home
- File a Police Report
- Public Works
- Transportation
- Transportation
- Transportation
- Transportation
- Transportation
- Transportation
- Engineering
- Transportation
- Utilities
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Utilities
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Public Works
- Climate Action Initiatives
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Public Works
- Climate Action Initiatives
- Recycling & Solid Waste
- Utilities
- Utilities
- Utilities
- Utilities
- Stormwater Quality
- Stormwater Quality
- Home
- Utilities
- Utilities
- City Departments
-
-
Community Development
-
Community Response
-
Convention and Cultural Services
-
Finance
-
Fire Department
-
Human Resources
-
Information Technology
-
Mayor and Council
-
Office of Public Safety Accountability
-
Office of the City Attorney
-
Office of the City Auditor
-
Office of the City Clerk
-
Office of the City Manager
-
Office of the City Treasurer
-
Police Department
-
Public Works
-
Utilities
-
Youth, Parks, & Community Enrichment
-
- Browse by categories
-
-
hiking Activities
-
pets Animals & Pets
-
domain_add Building & Planning
-
store Business
-
account_tree City Administration
-
category City Assets & Data
-
explore City Regions
-
diversity_4 Community Support
-
theater_comedy Culture & History
-
business_center Employment
-
directions Infrastructure
-
gavel Law, Code & Compliance
-
payments Money
-
park Outdoors & Sustainability
-
local_police Safety
-
directions_car Transportation
-
delete_sweep Utility Services
-
Use the menus above to navigate by City Departments or Categories.
You can also use the Search function below to find specific content on our site.
- Convention and Cultural Services
- Arts and Culture
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Home
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Convention and Cultural Services
- Access Leisure
- Recreation
- Youth, Parks, & Community Enrichment
- Community Engagement
- Community Engagement
- About YPCE
- Hart Senior Center
- Recreation
- Older Adult Services
- Youth, Parks, & Community Enrichment
- Long Range
- Youth, Parks, & Community Enrichment
- Recreation
- Recreation
- Home
- Youth, Parks, & Community Enrichment
- About YPCE
- About YPCE
- Older Adult Services
- Home
- Innovation and Grants
- Aquatics
- CCS Partners
- Innovation and Grants
- Convention and Cultural Services
- Community Engagement
- District 7 - Rick Jennings
- Request a Permit
- CCS Partners
- Fire Department
- About YPCE
- Convention and Cultural Services
- CCS Partners
- Emergency Management
- CCS Partners
- Commercial Waste Services
- Home
- Recreation
- Access Leisure
- Recreation
- Recreation
- Recreation
- Specialty Parks
- Specialty Parks
- Permits for YPCE
- Recreation
- Youth, Parks, & Community Enrichment
- About YPCE
- Youth, Parks, & Community Enrichment
- Aquatics
- Home
- Animal Care
- Animal Care
- Community Development
- Animal Care
- Animal Care
- Animal Care
- Animal Care
- Animal Care
- Specialty Parks
- Animal Care
- Animal Care
- City Government
- Community Development
- Building
- Contact CDD
- Building
- Building
- Building
- Building
- Business Waste Requirements
- Commercial Waste Services
- Maintenance Services
- Procurement Services Division
- Parks
- Utilities
- Public Works
- Engineering
- Fire Prevention
- Building
- Building
- Building
- Building
- Engineering
- Home
- Public Works
- Engineering
- Planning
- Fire Prevention
- Contact CDD
- Building
- Fire Prevention
- Engineering Programs & Services
- Fire Prevention
- Community Development
- Community Development
- Community Development
- Transportation
- Locate & Grow in Sacramento
- Planning
- Planning
- Planning
- Climate Action Initiatives
- Planning
- Planning
- Parks
- Community Development
- Community Development
- Planning
- List of City Manager's Office Projects and Programs
- Public Works
- Planning
- Planning
- Public Works
- Transportation
- Planning
- Planning
- Engineering
- 102-Acre Site
- Community Development Meetings and Hearings
- Major Planning Projects
- Locate & Grow in Sacramento
- Planning
- City Government
- Innovation and Economic Development
- Code Compliance
- Revenue Division
- Business
- Office of the City Manager
- Recycling & Solid Waste
- Business
- Business
- Procurement Services Division
- Revenue Division
- Business
- Revenue Division
- City Auditor Reports
- City Auditor Reports
- Cannabis Management
- Cannabis Management
- Business Operations Tax
- Cannabis Management
- Office of the City Manager
- Cannabis Management
- Cannabis Management
- Cannabis Management
- Parking
- COVID-19 Relief & Recovery
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Office of the City Manager
- Business
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- Office of the City Manager
- Business
- Finance
- Accounting Division
- Police Services
- Procurement Services Division
- City Government
- Code Compliance Programs
- Code Compliance Programs
- Commercial Waste Services
- Procurement Services Division
- Procurement Services Division
- Home
- Commercial Waste Services
- Procurement Services Division
- Finance
- Finance
- Procurement Services Division
- Office of the City Auditor
- Office of the City Auditor
- Office of the City Auditor
- Accounting Division
- Office of the City Clerk
- Home
- About YPCE
- Diversity and Equity
- Records Management
- Office of the City Auditor
- Director Hearings
- Director Hearings
- Director Hearings
- District 1 - Lisa Kaplan
- District 2 - Shoun Thao
- City Auditor Reports
- Office of the City Clerk
- About YPCE
- Police Transparency
- Home
- Records Management
- Office of the City Manager
- Office of the City Manager
- Office of the City Manager
- Neighborhood Directory
- Neighborhood Directory
- Community Engagement
- Office of the City Manager
- Office of the City Manager
- Office of the City Manager
- Office of the City Manager
- Home
- City Government
- Engineering
- City Government
- Long Range
- City Government
- City Government
- City Government
- City Government
- Information Technology
- Camp Sacramento
- Parking
- About YPCE
- Finance
- Drinking Water Quality
- Office of Public Safety Accountability
- Police Services
- Police Services
- Marina
- Police Services
- Contact Us
- Police Services
- Utilities
- Pay Your Utility Bill
- Office of the City Clerk
- Home
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Office of the City Clerk
- Mayor and Council
- Home
- Diversity and Equity
- Office of the City Auditor
- Office of Public Safety Accountability
- About the City Attorney's Office
- Office of the City Auditor
- Office of the City Auditor
- Police Department
- Maps and Geographic Information Systems
- Office of Public Safety Accountability
- Police Department
- City Government
- Office of the City Auditor
- 102-Acre Site
- 102-Acre Site
- Public Works
- About SPD
- Facilities & Real Property Management
- Public Works
- Adult Sports Activities and Resources
- Climate Action Initiatives
- Fleet Services
- Public Works
- Director Hearings
- Director Hearings
- Director Hearings
- Director Hearings
- General Plans
- Police Transparency
- Convention and Cultural Services
- Legislative Management
- Home
- Maps and Geographic Information Systems
- Office of the City Clerk
- Police Services
- Office of the City Auditor
- Office of Public Safety Accountability
- About the City Attorney's Office
- Office of the City Auditor
- Office of the City Auditor
- Police Department
- Maps and Geographic Information Systems
- Office of Public Safety Accountability
- Police Department
- City Government
- Office of the City Auditor
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Mayor and Council
- Maps and Geographic Information Systems
- Community Resources and Financial Empowerment
- Community Engagement
- Locate & Grow in Sacramento
- Major Planning Projects
- Engineering
- 102-Acre Site
- Community Development Meetings and Hearings
- Major Planning Projects
- Locate & Grow in Sacramento
- Planning
- Youth, Parks, & Community Enrichment
- Specialty Parks
- Long Range
- City Government
- List of City Manager's Office Projects and Programs
- Parking
- About YPCE
- Home
- Engineering Programs & Services
- Maintenance Services
- City Government
- Older Adult Services
- Home
- Youth, Parks, & Community Enrichment
- About YPCE
- About YPCE
- Older Adult Services
- Home
- 102-Acre Site
- Long Range
- City Auditor Reports
- Priority Projects/Investments
- Innovation and Economic Development
- Diversity and Equity
- Join Sacramento Fire
- Innovation and Economic Development
- Transportation
- Responding to Homelessness
- Office of the City Manager
- District 5 - Caity Maple
- Office of the City Manager
- Safety and Crime Prevention Tips
- Police Department
- Community Development Meetings and Hearings
- Diversity and Equity
- Older Adult Services
- Cannabis Management
- Office of the City Auditor
- Office of the City Auditor
- Human Resources
- Financial Empowerment
- Home
- Innovation and Economic Development
- Police Community Programs
- Community Response
- Community Response
- Workforce Development
- Police Community Programs
- Community Response
- Office of the City Manager
- Planning
- Housing
- Housing Development Toolkit
- Housing Development Toolkit
- Housing
- Housing
- Code Compliance
- Revenue Division
- Priority Projects/Investments
- Long Range
- About YPCE
- Older Adult Services
- Recreation
- Older Adult Services
- Youth, Parks, & Community Enrichment
- Older Adult Services
- Home
- District 5 - Caity Maple
- About the Office of the City Auditor
- Join Sacramento Fire
- Animal Care
- District 7 Resources
- Community Engagement
- Police Community Programs
- About YPCE
- Police Department
- Youth, Parks, & Community Enrichment
- Specialty Parks
- Aquatics Programs
- District 7 Resources
- Youth, Parks, & Community Enrichment
- CCS Partners
- Join Sacramento Fire
- About YPCE
- Aquatics Programs
- Recreation
- Aquatics
- Youth, Parks, & Community Enrichment
- Police Community Programs
- Youth, Parks, & Community Enrichment
- Youth, Parks, & Community Enrichment
- Police Community Programs
- Youth, Parks, & Community Enrichment
- Recreation
- Youth, Parks, & Community Enrichment
- Home
- Convention and Cultural Services
- Arts and Culture
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Convention and Cultural Services
- Home
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Arts and Culture
- Convention and Cultural Services
- Innovation and Grants
- Aquatics
- CCS Partners
- Innovation and Grants
- Convention and Cultural Services
- Community Engagement
- District 7 - Rick Jennings
- Request a Permit
- CCS Partners
- Fire Department
- About YPCE
- Convention and Cultural Services
- CCS Partners
- Emergency Management
- CCS Partners
- Commercial Waste Services
- Home
- Convention and Cultural Services
- About the City Attorney's Office
- Specialty Parks
- Planning
- About Sacramento Fire
- CCS Partners
- Public Works
- Police Department
- Cannabis Management
- Office of the City Auditor
- Office of the City Auditor
- Human Resources
- Financial Empowerment
- Home
- Innovation and Economic Development
- Police Community Programs
- Human Resources
- Human Resources
- Human Resources
- Human Resources
- Home
- Human Resources
- Payroll Division
- Camp Sacramento
- HR Documents & Resources
- Human Resources
- Human Resources
- Home
- District 7 Resources
- Fire Department
- Leisure Enrichment
- Employee & Retiree Benefits
- Police Services
- START
- Passage Middle School Program
- District 5 - Caity Maple
- About the Office of the City Auditor
- Join Sacramento Fire
- Animal Care
- District 7 Resources
- Community Engagement
- Police Community Programs
- About YPCE
- Police Department
- Innovation and Economic Development
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Current Transportation Efforts, Plans and Programs
- Utilities
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Utilities
- Information Technology
- Information Technology
- City Government
- Information Technology
- Information Technology
- Information Technology
- Information Technology
- Home
- Fire Operations
- Information Technology
- Information Technology
- Collection Calendar
- City Government
- Information Technology
- Infrastructure Finance Division
- Home
- Infrastructure Finance Division
- Finance
- Infrastructure Finance Division
- Infrastructure Finance Division
- Building Programs
- Utilities
- Utilities
- Office of the City Manager
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Safety Tips
- Construction Coordination
- Transportation
- Transportation
- Utilities
- Public Works
- Public Works
- Police Community Programs
- Utilities Projects
- Home
- Survey Services
- Maintenance Services
- Utilities Projects
- Maintenance Services
- Maintenance Services
- Curbside Collection Services & Rates
- Tree Permits and Ordinances
- Public Works
- Transportation
- Transportation
- Engineering
- Transportation
- Transportation
- Park Planning & Development
- Parks
- Public Works
- Transportation Projects
- Parks
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Utilities
- Utilities
- Utilities
- Utilities
- Stormwater Quality
- Stormwater Quality
- Home
- Utilities
- Utilities
- Community Development
- Community Development
- Code Compliance
- Code Compliance
- Community Development
- Code Compliance
- Code Compliance
- Community Development
- Fire Prevention
- Code Compliance
- Recycling & Solid Waste
- Code Compliance
- Residential Permit Parking (RPP)
- Code Compliance
- Fire Prevention
- Contact CDD
- Building
- Fire Prevention
- Engineering Programs & Services
- Fire Prevention
- Commercial Waste Services
- Cannabis Management
- City Government
- Commercial Waste Services
- Recycling & Solid Waste
- Disabled Person Parking
- Fire Code Enforcement
- Commercial Waste Services
- Contact Parking Services
- Residential Permit Parking (RPP)
- Community Development
- Request a Permit
- Request a Permit
- Fire Prevention
- Contact CDD
- Public Records
- Code Compliance
- Cannabis Management
- Request a Permit
- Request a Permit
- City of Festivals
- Engineering
- Request a Permit
- Housing Development Incentives
- Arts and Culture
- Housing Development Incentives
- Public Works
- Public Works
- Building
- Youth, Parks, & Community Enrichment
- Locate & Grow in Sacramento
- Building
- Request a Permit
- Revenue Division
- Revenue Division
- Commercial Waste Services
- Building Programs
- Urban Forestry
- Planning
- Finance
- Accounting Division
- Home
- Accounting Division
- Payroll Division
- Curbside Collection Services & Rates
- Office of the City Manager
- Finance
- Budget Division
- Budget Division
- Home
- Hart Senior Center
- Recycling & Solid Waste
- Discount Deals
- Water Conservation
- Aquatics
- Finance
- Pay Your Utility Bill
- Utility User Tax
- Office of the City Treasurer
- Office of the City Treasurer
- Home
- Office of the City Treasurer
- Parking
- COVID-19 Relief & Recovery
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Innovation and Economic Development
- Office of the City Manager
- Business
- Business
- Innovation and Economic Development
- Innovation and Economic Development
- Business
- Innovation and Economic Development
- CORE
- Innovation and Grants
- Convention and Cultural Services
- Stormwater Quality
- Economic Gardening
- Arts and Culture
- Innovation and Grants
- Recycling & Solid Waste
- Youth, Parks, & Community Enrichment
- Engineering
- Infrastructure Finance Division
- Home
- Infrastructure Finance Division
- Finance
- Infrastructure Finance Division
- Infrastructure Finance Division
- Building Programs
- Office of the City Treasurer
- Office of the City Treasurer
- Home
- Office of the City Treasurer
- Building
- Cannabis Business Operating Permits
- Revenue Division
- Development Standards
- Recycling & Solid Waste
- Development Standards
- Finance
- Community Engagement
- Marina
- Household Hazardous Waste
- Public Works
- Community Development
- Revenue Division
- Utilities
- City Government
- Finance
- Animal Care
- Home
- Development Standards
- Marina
- Revenue Division
- Permits for YPCE
- Revenue Division
- Infrastructure Finance Division
- Home
- Workforce Development
- List of City Manager's Office Projects and Programs
- About YPCE
- Revenue Division
- Budget Division
- Revenue Division
- Revenue Division
- Transportation
- Utilities Projects
- Climate Action Initiatives
- Housing
- Public Works
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Public Works
- Home
- Access Leisure
- Recreation
- Climate Action and Sustainability
- Climate Action and Sustainability
- Public Works
- Climate Action and Sustainability
- Climate Action and Sustainability
- Planning
- Fleet Services
- Climate Action and Sustainability
- Procurement Services Division
- Business Waste Requirements
- Permit Services
- Utilities
- Climate Action and Sustainability
- Utilities
- Recreation
- About YPCE
- Public Works
- Youth, Parks, & Community Enrichment
- About YPCE
- Commercial Waste Services
- Permits for YPCE
- About YPCE
- Home
- Current Transportation Efforts, Plans and Programs
- Recreation
- Access Leisure
- Recreation
- Recreation
- Recreation
- Specialty Parks
- Specialty Parks
- Permits for YPCE
- Recreation
- Youth, Parks, & Community Enrichment
- About YPCE
- Youth, Parks, & Community Enrichment
- Aquatics
- Home
- Park Planning & Development
- Parks
- Public Works
- Transportation Projects
- Parks
- Transportation Projects
- Transportation Projects
- Transportation Projects
- Urban Forestry
- Parks
- Public Works
- Parks
- Home
- Urban Forestry
- Urban Forestry
- Urban Forestry
- Climate Action Initiatives
- Maintenance Services
- Safety Tips
- Office of the City Manager
- Specialty Parks
- Community Response
- Community Response
- Home
- Office of the City Manager
- Contact Us
- Contact Us
- Crime and Safety
- Crime and Safety
- Crime and Safety
- Crime and Safety
- Crime and Safety
- Police Services
- Fire Prevention
- Crime and Safety
- Police Services
- Crime and Safety
- Pay Your Utility Bill
- Crime and Safety
- Office of the City Auditor
- City Auditor Reports
- Fire Prevention
- Office of the City Manager
- Fire Department
- Join Sacramento Fire
- Crime and Safety
- Emergency Management
- Fire Department
- Fire Department
- Fire Department
- Home
- Fire Department
- Fire Department
- Fire Department
- Home
- Fire Department
- Fire Prevention
- Contact CDD
- Building
- Fire Prevention
- Engineering Programs & Services
- Fire Prevention
- Request a Permit
- Request a Permit
- Police Services
- Police Services
- Request a Permit
- Request a Permit
- Police Services
- Police Department
- Request a Permit
- Police Services
- Police Services
- Police Services
- Police Services
- Public Information Office
- Police Services
- Home
- Police Department
- Home
- Police Department
- Police Department
- Request a Permit
- Police Services
- Police Services
- Police Services
- Police Services
- Police Services
- Police Services
- Police Department
- Emergency Management
- Police Department
- Information Technology
- Flood Preparedness
- Fire Department
- Utilities
- Utilities
- Office of the City Manager
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Safety Tips
- Safety Tips
- Office of the City Manager
- Specialty Parks
- Transportation
- Utilities Projects
- Climate Action Initiatives
- Housing
- Public Works
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Current Transportation Efforts, Plans and Programs
- Public Works
- Home
- Transportation Technology
- Parking
- Fleet Services
- Climate Action Initiatives
- Current Transportation Efforts, Plans and Programs
- Police Services
- Marina
- Marina
- Public Works
- Housing
- Home
- Curbside Collection Services & Rates
- Sacramento Valley Station
- Public Works
- Long Range
- Current Transportation Efforts, Plans and Programs
- Transportation
- Public Works
- Home
- File a Police Report
- Public Works
- Transportation
- Transportation
- Transportation
- Transportation
- Transportation
- Transportation
- Engineering
- Transportation
- Utilities
- Utilities
- Utilities
- Utilities
- Utilities
- Home
- Utilities
- Utilities
- Utilities
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Public Works
- Climate Action Initiatives
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Recycling & Solid Waste
- Public Works
- Climate Action Initiatives
- Recycling & Solid Waste
- Utilities
- Utilities
- Utilities
- Utilities
- Stormwater Quality
- Stormwater Quality
- Home
- Utilities
- Utilities
Search for content
Social Engineering
Social Engineering is by far the most common technique used by threat actors to manipulate people into performing actions or divulging information they are after.
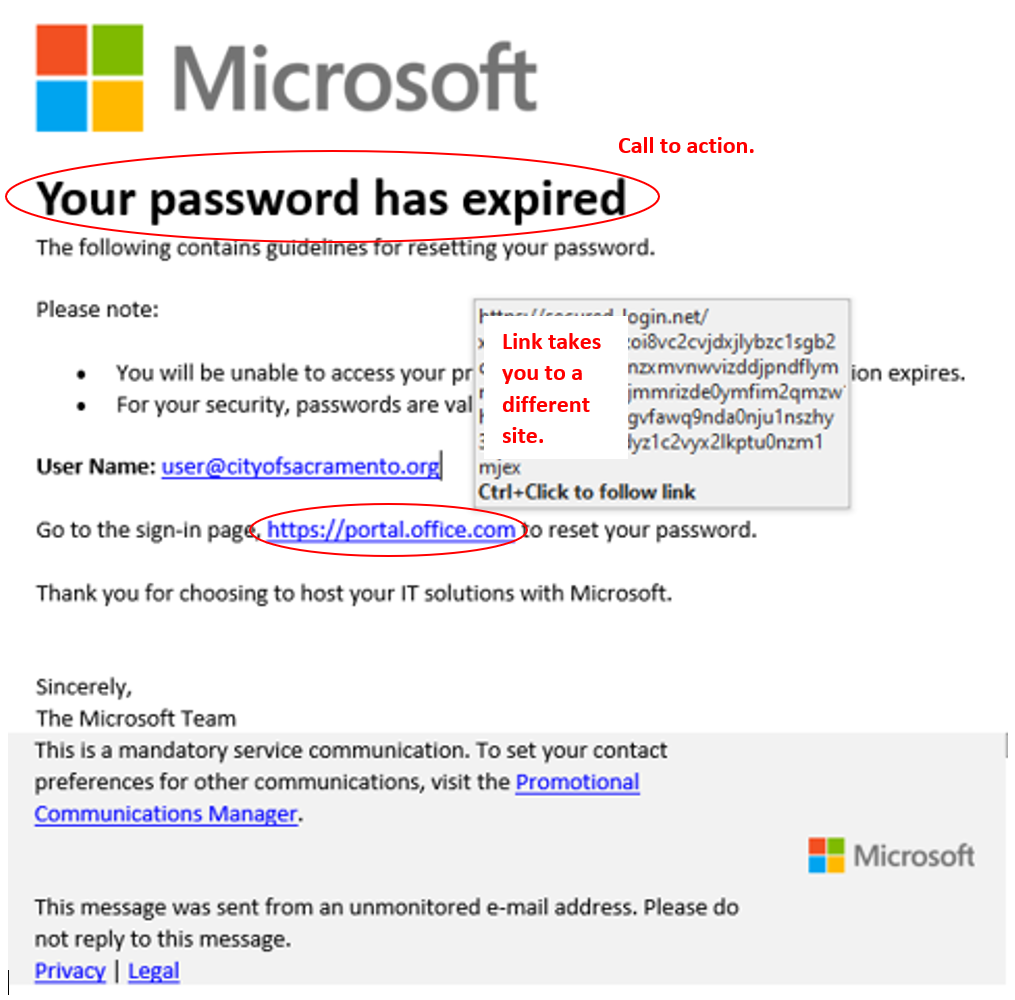
Phishing
Is the practice of sending emails purporting to be from reputable companies in order to induce individuals to act, reveal personal information, such as passwords and credit card numbers.
Tell-tale signs of a phishing email
- An unfamiliar greeting.
- Grammar errors and misspelled words.
- Email addresses and domain names that don't match.
- They mimic a trusted domain (i.e., “rnicrosoft.com” instead of “microsoft.com”).
- Unusual content or request – these often involve a transfer of funds or requests for login credentials.
- Urgency – ACT NOW, IMMEDIATE ACTION REQUIRED.
 open_in_full
open_in_full
How to protect yourself from phishing:
- Be cautious and suspicious of any email that asks you to provide login credentials or financial information.
- Do not open links or attachments from suspicious emails. It may contain malware or direct you to a fake website that is designed to steal your information.
- Verify the authenticity of the emails by reaching out to the organization through a verified phone, email, or website.
- Disregard and report/block the suspicious email.
- Keep your software up to update. Software updates contain security patches that can help protect against the latest threat.
Report phishing
- You can report phishing to Anti-Phishing Working Group (APWG) by sending a sample of the phishing email to: phishing-report@us-cert.gov
- You can follow FTC How To Block Unwanted Calls | Consumer Advice (ftc.gov) guidelines to block unwanted calls.
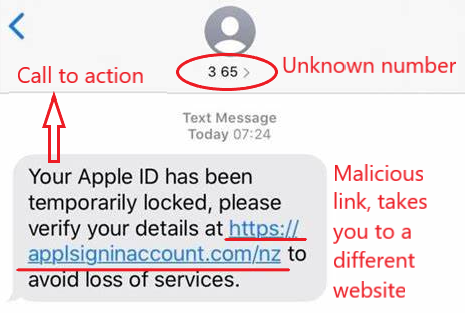
Smishing
Is a type of practice that involves sending text messages (SMS) or other forms of text-based communication, such as WhatsApp messages or any social media messages, to trick victims into revealing personal or sensitive information, downloading malicious software or visiting fraudulent websites.
Tell-tale signs of a smishing email
- Unfamiliar sender or phone number. May appear as a well-known company or organization but the sender’s information may be spoofed.
- Urgency or a sense of pressure (i.e., “Act now, Account needs immediate attention!”, “limited time offer!”).
- Suspicious links or attachments. Contain links to malicious websites or attachments when clicked and download malware on the device.
- Request for personal information and asks for sensitive personal or financial information. Legitimate organizations will not typically request this information.
- Contains poor grammar and spelling errors.
 open_in_full
open_in_full
How to protect yourself from Smishing:
- Be cautious and avoid clicking on links or downloading attachments.
- Verify the authenticity of the message.
- Do not provide any personal or financial information.
- Disregard and block the number.
- In an event you provided your financial information to a scammer, contact your financial institution and cancel fraudulent transactions and block future charges.
Report smishing
- If you got a Smishing text message, forward it to SPAM (7726) and follow FTC’s guideline How to Recognize and Report Spam Text Messages | Consumer Advice (ftc.gov)
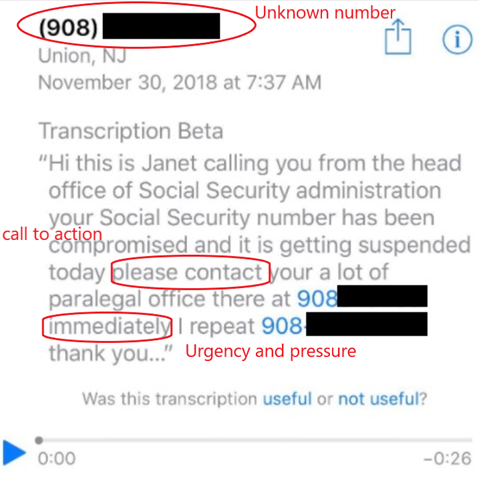
Vishing
Is a type of practice that involves a scammer using voice communication, typically over the phone, to trick someone into revealing sensitive information, such as bank account numbers, social security numbers or credit card numbers. Vishing attacks involve an automated phone call or live caller pretending to be from a legitimate organization. Attackers will use various techniques to gain the victims trust and convince them to divulge sensitive information.
Tell-tale signs of a vishing email
- Unusual offer or requests that seem too good to be true, such as large sums of money or prize in exchange of providing personal information or performing certain actions. Legitimate organizations will not typically request this information.
- Urgency or a sense of pressure. Often include urgent language to make recipient feel like they need to act quickly.
- Attackers may threat or intimidate to scare victims providing information or action.
- Caller ID Spoofing. The caller ID may be spoofed, making it look like the call is coming from a legitimate organization.
- Poor call quality or technical issues. Attackers may use technology that distorts their voice or causes the call quality to be poor.
 open_in_full
open_in_full
How to protect yourself from Vishing:
- Be wary of unsolicited calls. If you receive a call from unknown number, be cautious and do not provide any personal information. Do not trust caller ID.
- Verify authenticity of the call. If the caller claimed to be from a legitimate organization, contact the organization directly through a verified phone number or website to confirm legitimacy of the call.
- End the call if the caller is suspicious, do not engage in conversation. Use call-blocking and filtering tools to prevent unwanted or suspicious calls from reaching you.
- In an event you provided your financial information to a scammer, contact your financial institution and cancel fraudulent transactions and block future charges.
Report vishing
- You can report vishing numbers to FTC and add your phone number to the list for free to prevent from unwanted sales call National Do Not Call Registry
- You can follow FTC How To Block Unwanted Calls | Consumer Advice (ftc.gov) guidelines to block unwanted calls.
ON THIS PAGE
